We are currently working on a project to provide abuse monitoring information to our customers.
Giving our customers just the raw data is not helpful, so our goal is to contextualize the data.
We still have long ways to go, but the basics are there.
So what do I see right now on our platform?
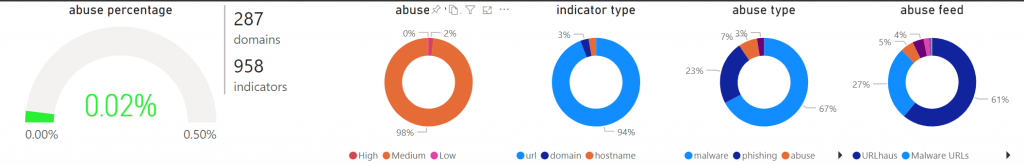
- Malware (67%)
- Phishing (23%)
- The rest falls into somewhat general buckets like BEC fraud, DGA, botnets, dark lists, crypto mining, etc. Very low incidental percentages.
The above-mentioned data is from two years of monitoring.
On the left is displayed the overall abuse percentage since 2018. And yes, the abuse levels are low, certainly if you compare them with the registrar statistics from Spamhaus.
Malware is the biggest problem.
The number of domains used in malware is low (2.71%).
However, the number of URL’s is high (94.24).
When I dive into information, it becomes clear that Emotet a “Crime As A Service” is the biggest threat actor (operational since 2014).
Emotet does not get noticed much by registrars. Due to tactics, techniques, and procedures (TTP) used by these criminals, they do not require domain names. Meaning there is no registration data; there is no money trail; there is simply nothing at the registrar level.
Emotet hacks web and hosting services to deploy their malicious payload and essentially operates a botnet through these hacked services.
I think, however, that when we release contextual information, things will change. I suspect that situational awareness will provide enough info for our customers to harden security.
Currently, we are fine-tuning the data we download from https://pulsedive.com.
Pulsedive will provide our customers with a more granular level of detail. The data provided at Pulsedive is usually used by Security Operation Center Analysts to turn information into actionable intelligence.