Why your domain registration just got smarter: introducing RDAP
In today's digital world, your domain name is more than just a web address—it's your online identity. That's why we're excited to tell you about RDAP (Registration Data Access Protocol), a significant upgrade in how your domain registration information is handled and protected. This new protocol isn't just a technical update; it's about giving you more control, better security, and a smoother experience managing your online presence.

Your privacy, your control
Remember when social media platforms revolutionized privacy settings, letting you choose exactly what information you share with whom? RDAP will …
In this article/faq, I will explain the security threat dashboarding/monitoring.
What is it?
In the first beta phase, we will make the threat intelligence we download from Pulsedive available to our customers in the domain manager.
If you are a customer of Realtime Register you can join the beta program.
Please contact our support team for information.
As a customer, you will be able to see the active security threats.
Security threats could be phishing domain names or malware domain names.
The Abuse Dashboarding provides you with information that usually does not get reported to Registrars.
As a result, you …
We are currently working on a project to provide abuse monitoring information to our customers.
Giving our customers just the raw data is not helpful, so our goal is to contextualize the data.
We still have long ways to go, but the basics are there.
So what do I see right now on our platform?
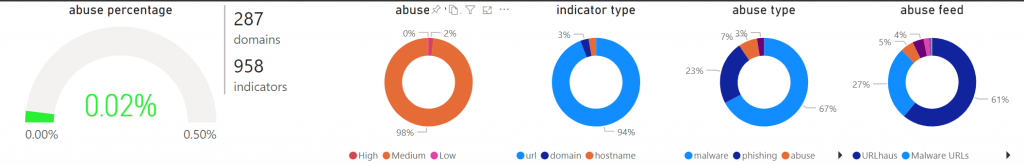
- Malware (67%)
- Phishing (23%)
- The rest falls into somewhat general buckets like BEC fraud, DGA, botnets, dark lists, crypto mining, etc. Very low incidental percentages.
The above-mentioned data is from two years of monitoring.
On the left is displayed the overall abuse percentage since …
We released a few new features, one of them, RDAP reseller Vcard.
To further streamline abuse reports & disclosure requests, Realtime Register introduces the Abuse Vcard. This Vcard will display your (reseller role) abuse contact details through RDAP.
Showing your (external) abuse contact information will increase the speed of abuse reporting.
Internal abuse email address/information.
Resellers can also enter abuse contact information for our abuse & support staff.
We are not setting requirements here for our resellers, but it would be good if this email address is monitored 24/7. We intend to use this info for emergency communications when dealing …
“Behavior reflects personality. The best indicator of future violence is past violence. To understand the “artist,” you must study his “art.” The crime must be evaluated in its totality. There is no substitute for experience, and if you want to understand the criminal mind, you must go directly to the source and learn to decipher what he tells you. And, above all: Why + How = Who.”
― John E. Douglas, Mindhunter: Inside the FBI’s Elite Serial Crime Unit
The above quote is also applicable when you deal with cybercrime investigations. Though registrars usually do not deal with serial killers, …
Today we introduce a new account setting called:”Default Privacy Protect setting”, which you can access by clicking here.
Setting disabled.
When selected, domain name registrations and transfers will not use our privacy service automatically. This is how it used to work for years.
Setting enabled when free (and available)
When enabled all domain name registrations and transfers will automatically use our privacy service. Regardless if you use WHMCS, our API or the domain name manager.
A list of available TLDs that can be used for this service is located here.
We keep recommending this service as it is unknown if …
Update: 25-05-2018
The procedure below is now live as per the ICANN temporary spec. I observe that not every Registrar was aware of the below situation. If you cannot transfer out your domain name(s) advise the gaining registrar to stop parsing WHOIS data and trying to send FOA emails to the registrant or admin contact, this will no longer work.
The new procedure has been communicated last week by ICANN to all registrars. To view this communication click here,
As mentioned in a previous blog the WHOIS will change drastically over the next few weeks.
At …
After twelve months of endless discussions and a looming deadline, ICANN received information from the Art 29 Working Party.
The EU Data Protection Authorities will not grant ICANN forbearance regarding the May 25th deadline when it comes to the WHOIS. Again the DPA’s re-confirmed their advise towards ICANN and does not deviate much from the advice they have provided ICANN since 2000.
The full press release from ICANN and the Article 29 WP letter can be read here.
Now that it is official there will be no forbearance regarding WHOIS, which was a silly request to begin with, …
Last week we received a lot of positive comments regarding our GDPR TLD matrix. And we had a lot of requests to get access to the matrix.
As a push to create more GDPR awareness, we decided to publish our API on the website for the public, including the GDPR TLD matrix.

You can enter the matrix here.
Keep in mind the matrix has been developed with the Realtime Register processes in mind and in some instances cannot be merely be pasted and copied.
One comment which we received a lot last week was:”wow there are so many …
On September 26 we will release a revamped version of our privacy protection service. It contains significant changes and will comply with upcoming EU GDPR and ICANN policies.
Why you need the new privacy protect service
At Realtime Register we value the privacy of your customers the registrants, by using the new Realtime Register privacy protect services you’ll bring your customers privacy to the highest level possible. Regarding domain names, it will enable you to be GDPR ready, saving you a lot of time in this area.
The new privacy protect service:
- is free!That is, for reselling customers with …



