Key benefits
Realtime Register has invested heavily in a system to monitor abusive domains, allowing us to quickly detect abuse, report on it, and recommend steps you can take. Together we make the internet safer. But above all, we prevent reputation damage for you and your customers, that otherwise can assume huge proportions. Use of the Realtime Register Abuse Monitoring & Reporting is FREE OF CHARGE for all domains registered/managed on our platform!
Request a demo1
Abuse Dashboard
75+
Intelligence feeds
120+
Open Threat Exchange feeds
2000+
Domain extensions
Opportunities for your business
Domain Abuse is a big problem in our industry and occurs in many different ways: botnets, phishing, child pornography, malware, illegal pharmacies, CEO fraud, etc.
The responsibility for detecting and combating domain abuse is increasingly being shifted towards the registries, registrars, and the hosting provider. Yet completely preventing abuse is difficult, if not impossible. There will always be registrants who register a domain with (eventually) bad intentions. The trick is to recognize these registrants, monitor their actions, and intervene as quickly as possible when they develop illegal activities. If taken offline quick enough, they will stop or seek refuge elsewhere.
Abuse monitoring & reporting for a safer internet
- Show your customers and employees you take domain abuse very seriously
- Abuse Insights unlocks unparalleled information for you and your customers to obtain insights into what types and abuse levels are ongoing in your domain portfolio
- The abuse dashboard allows you to tap into the abuse monitoring system yourself. You can see how much abuse we have detected on your domain portfolio, what has been reported by the different abuse feeds we use, and take pre-emptive action
- Add users that should receive a notification when we detect an abuse case in your portfolio
- Our abuse fighting results in better promos and higher MDFs! Increasingly, abuse performance and abuse mitigation attitude are considered when setting special promo prices and awarding MDF funds. Because we monitor all domain registrations and always take action in case of (possible) abuse, we are able to realize better promos and higher MDFs for our resellers
- Please see the testimonials of GMO Registry and RADIX Registry below
Abuse monitoring & reporting FREE OF CHARGE!
Registry Referral for fighting abuse together


Features
Hourly updates
Almost real-time threat intelligence is delivered through our API or email notifications. Providing the ability to process threat intelligence straight into your ticketing system.
ICANN RRA Spec. 11.3B compliancy
Total DNS Abuse Overview on all levels. Detects spam, phishing, malware, botnets and pharming.
Zoom in functionality
Zoom in per abuse case on number of feeds reporting the abuse and detailed information provided by the feed used.
Extensive abuse sourcing
75+ blocklists and intelligence feeds and 120+ open thread exchange feeds.
Automated notifications
Automated notifications for new abuse cases.
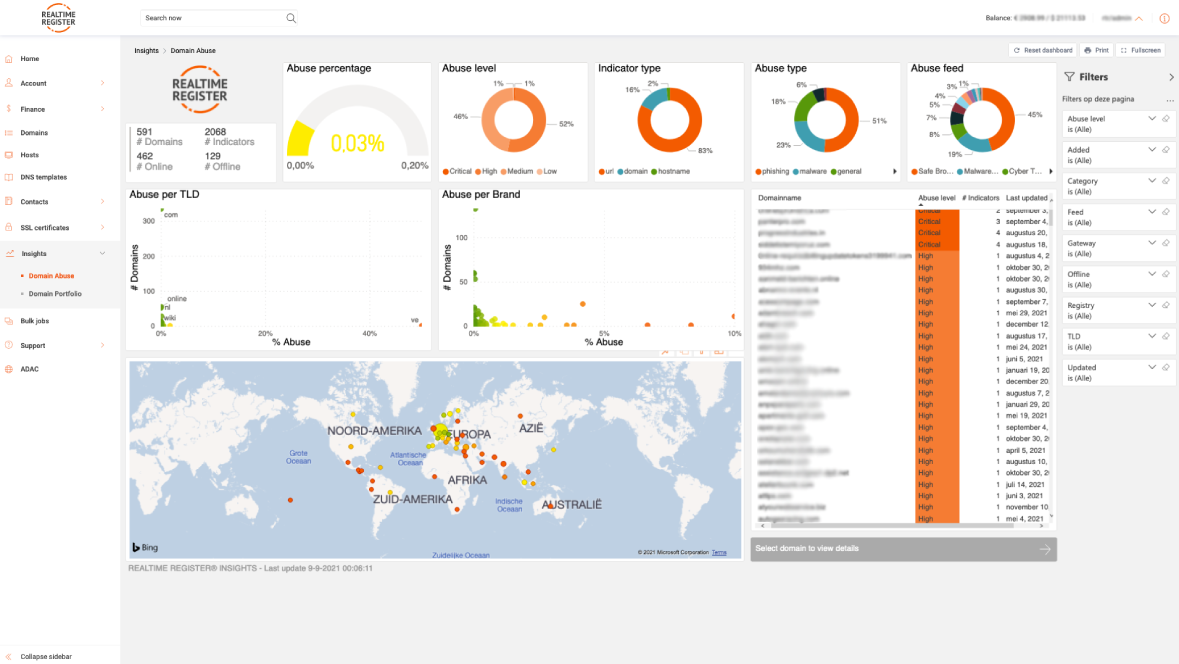
Extensive dashboard
Dashboard with abuse percentage, abuse level, indicator type, abuse type, abuse feed, abuse per TLD and per brand.
Abuse Policy
Realtime Register is an active member of the internet community in the fight against abuse. We are among the initial signatories of the DNS Abuse Framework (http://dnsabuseframework.org/) and follow the framework in our abuse policy regarding domain abuse. The framework applies to identify the following types of domain abuse.
- Botnets
- Phishing
- Pharming
- Spam
- CSAM (Child Sexual Abuse Material)
Besides the DNS Abuse Framework, we are also proudly member of:
- Global Cyber Alliance
- topDNS Initiative
- Cyber Threat Coalition
- Covid-19 Cyber Threat Intelligence League
- ECO/I2Coalition
- Internet Infrastructure (I2) Coalition
URL/Hostname/content abuse is foremost the responsibility of the hosters (our customers) who are better positioned to battle these types of abuse. We assist our customers with resources, notifications, monitoring and consultancy. We also offer services where we act as first responders to abuse notifications on behalf of our customers, always within guidelines agreed upon with the customer.
Notice and takedown procedures
Most of these procedures are documented within the DNS Abuse Framework.
Realtime Register staff follows an incident reporting-based approach. If we receive a complaint, we determine the threat type and threat level. In our assessment, we investigate if more domain names are involved. After our staff has obtained all the available information, we apply the OODA loop. The OODA loop is a cyber intelligence strategy about the decision-making process. Broken down, the OODA loop stands for four distinct yet interrelated, smaller loops: observe, orient, decide, and act. Usually the result of this cyber intelligence approach is that we inform the customer to take down the malicious URL, or we inform the customer with the evidence why a domain name was taken down. These actions and processes are aligned with the relevant sections in our terms of service.
Terms and conditions